ci: add trivy security scanning step
Created by: ggilmore
Fixes #25645 (closed)
This PR adds the Trivy security scanning tool to our buildkite pipelines. The motivation behind this PR can be found in RFC 468: Container Vulun Scanning.
This PR adds the core logic to our CI pipeline to have Trivy run. There will be follow up work later on to have a process that pushes vulnerability reports to the @sourcegraph/security team's JIRA board for them to manage and triage.
When does Trivy run?
Trivy runs in the same three cases that cause our complete set of Docker images to be built (see https://github.com/sourcegraph/sourcegraph/pull/25756/files#diff-f25e7ee7447fb64c15ac6cb7c50e32e24497f60b316698ae2ff0448551d3f07e):
- commits to the default
mainbranch - commits to branches prefixed by
main-dry-run/ - commits to branches prefixed by
docker-images-patch/$IMAGE(where you want to only build a single image)
Right now, Trivy is set to not fail a build if it finds vulnerabilities. Specifically:
- docker images will still be built/pushed
- rollouts will still occur for sourcegraph.com + k8s.sgdev.org.
In the near future (~1 month's time), we will make a change to have Trivy block builds and rollouts once there is a more robust vulnerability management process in place.
(Note that Trivy will still soft-fail the step so that you can easily see the result in the buildkite logs).
What does Trivy scan for?
trivy-scan-high-critical.sh
This scan looks only looks for high / critical CVEs that have a known solution (this was the success criteria that was defined in RFC 468: Container Vulun Scanning).
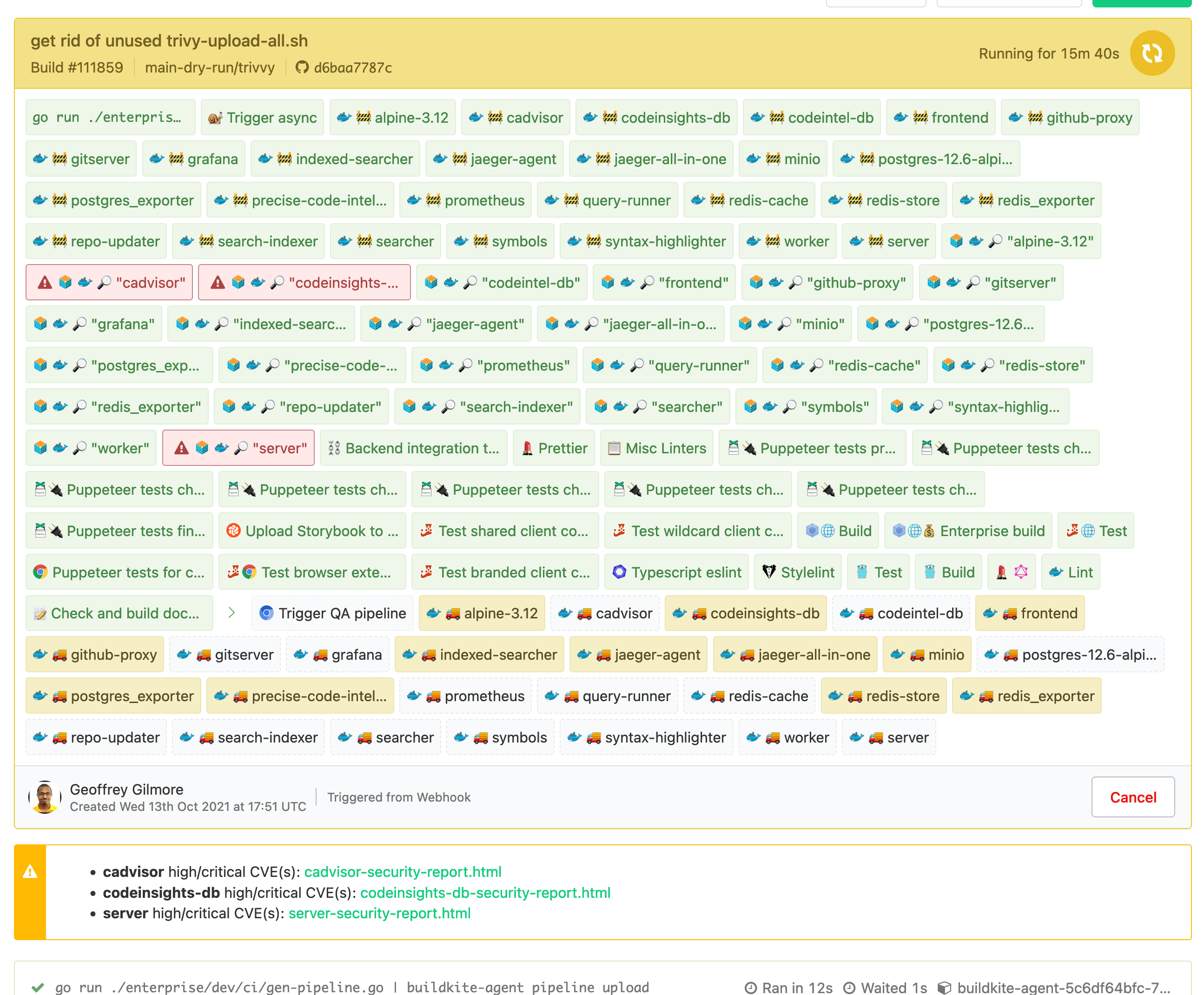
(Link to buildkite build for the above screenshot)
If the script finds anything with the above criteria, it'll upload a buildkite annotation with the results. The annotation consists of a simple lists with separate html pages with the results. Note that the buildkite annotation api doesn't make it straightforward to make it appear closer to a proper table, but this seemed good enough for now (given that this PR is a stepping stone for future work).
As stated before, Trivy will soft-fail a step to make it easy to pick out the failing step without actually failing the build as a whole.
Future plans
The next thing we'll work on is adding a process to pushing all known vulnerabilities (regardless of severity or whether or not there is a known fix) to the @sourcegraph/security team's JIRA board.